We may not have the course you’re looking for. If you enquire or give us a call on 01344203999 and speak to our training experts, we may still be able to help with your training requirements.

close
Press esc to close

close


Press esc to close

close
Fill out your contact details below and our training experts will be in touch.



Back to Course Information
Module 1: Threat Landscape and Incident Readiness
Module 2: Remote Triage and Its Tools
Module 3: Acquiring Memory and Disk Imaging
Module 4: Network Security Monitoring
Module 5: Event Log, Memory, and Malware Analysis
Module 6: Disk Forensics and Lateral Movement Analysis
Module 7: Continuous Improvement and Proactive Activities


This Incident Response training prepares individuals and teams to effectively manage and mitigate cybersecurity incidents. This course will benefit the following professionals:
There are no formal prerequisites for this Incident Response Training Course. However, prior experience in computer systems or related roles is recommended but not mandatory. Also, familiarity with programming might prove to be beneficial for the delegate.
Incident Response Training provides a structured approach to managing the aftermath of a security breach or cyberattack. Whether it's a computer incident, an IT incident, or a security incident, Incident Response aims to minimise damage, reduce recovery time and costs, and mitigate future risks. In an era where cyber threats are pervasive, mastering incident response is essential for organisations looking to protect their assets.
Proficiency in Incident Response is crucial for professionals in roles such as Incident Responders, Cybersecurity Analysts, and IT Security Managers. Having the skills to respond effectively to security incidents is a career game-changer. Organisations worldwide seek individuals who can swiftly and competently address incidents, making it a highly lucrative skill set in the cybersecurity domain.
The Knowledge Academy's 1-day Incident Response training equips delegates with the knowledge and techniques needed to effectively respond to security incidents. Under the guidance of an experienced trainer, participants will gain insights into attacker motivations, incident readiness, and the tools required for successful response.
Course Objectives:
Upon completing this course, delegates will possess the knowledge and skills required to identify and respond to security incidents, making them valuable assets in the cybersecurity landscape and opening doors to high-paying positions in international organisations.




Why choose us
Our easy to use Virtual platform allows you to sit the course from home with a live instructor. You will follow the same schedule as the classroom course, and will be able to interact with the trainer and other delegates.
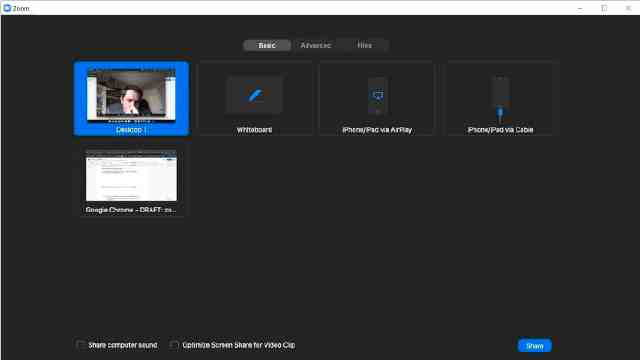
Our fully interactive online training platform is compatible across all devices and can be accessed from anywhere, at any time. All our online courses come with a standard 90 days access that can be extended upon request. Our expert trainers are constantly on hand to help you with any questions which may arise.
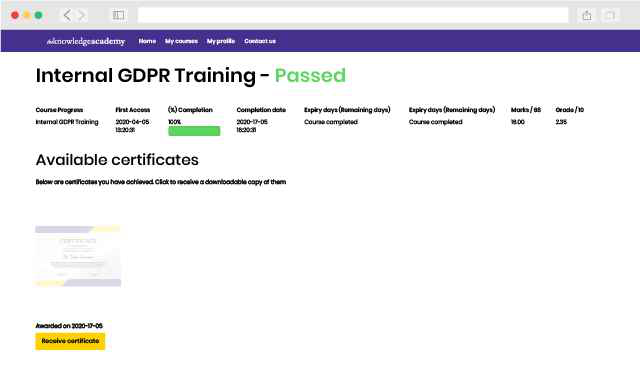
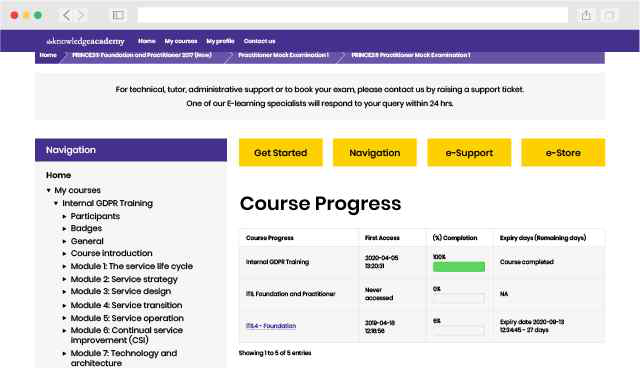
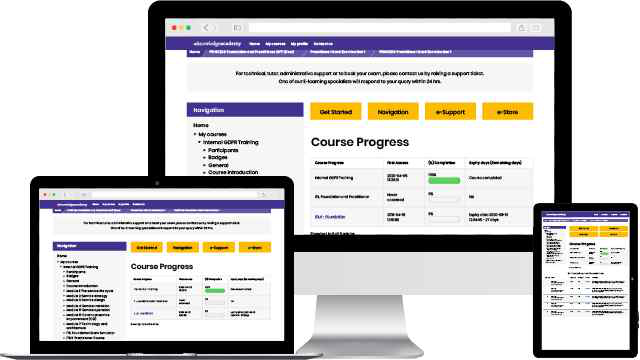
This is our most popular style of learning. We run courses in 1200 locations, across 200 countries in one of our hand-picked training venues, providing the all important ‘human touch’ which may be missed in other learning styles.

All our trainers are highly qualified, have 10+ years of real-world experience and will provide you with an engaging learning experience.

We only use the highest standard of learning facilities to make sure your experience is as comfortable and distraction-free as possible

We limit our class sizes to promote better discussion and ensuring everyone has a personalized experience

Get more bang for your buck! If you find your chosen course cheaper elsewhere, we’ll match it!
This is the same great training as our classroom learning but carried out at your own business premises. This is the perfect option for larger scale training requirements and means less time away from the office.

Our courses can be adapted to meet your individual project or business requirements regardless of scope.

Cut unnecessary costs and focus your entire budget on what really matters, the training.

This gives your team a great opportunity to come together, bond, and discuss, which you may not get in a standard classroom setting.

Keep track of your employees’ progression and performance in your own workspace.

You won't find better value in the marketplace. If you do find a lower price, we will beat it.

Flexible delivery methods are available depending on your learning style.

Resources are included for a comprehensive learning experience.




"Really good course and well organised. Trainer was great with a sense of humour - his experience allowed a free flowing course, structured to help you gain as much information & relevant experience whilst helping prepare you for the exam"
Joshua Davies, Thames Water



 Back to course information
Back to course information
We may not have any package deals available including this course. If you enquire or give us a call on 01344203999 and speak to our training experts, we should be able to help you with your requirements.
 If you miss out, enquire to get yourself on the waiting list for the next day!
If you miss out, enquire to get yourself on the waiting list for the next day!